Bad Idea: All Sensors, All Shooters, All the Time – a Joint All-Domain Command and Control System That Prioritizes Centralization
Joint All-Domain Command and Control (JADC2) is touted as an innovative upgrade to the military’s command and control structure for the modern age of warfare: an integrated network linking kinetic platforms; intelligence, surveillance, reconnaissance assets; and command and control nodes across a wide-ranging, all-domain battlefield. This all-seeing interplay will allow for unprecedented sharing of data and information, allowing for kill chains that spread across thousands of miles and up and down all echelons of warfighting. Centralized clouds, resilient operational systems, and long-distance communications pathways are often held up as examples of the technology needed to make this a reality.
This high-level consolidation and integration sounds like a great idea but is actually a bad one if its proponents continue to prioritize the idea of a centralized architecture across a wide battlespace. The reality is any expected fight with an adversary like China will include the degradation of battlefield information and consequent loss of the centralization for which JADC2 appears to be designed. Instead, a joint command and control structure should be reimagined as an architecture biased toward a likely collapse to the tactical unit or task group level — allowing the system to be rebuilt to facilitate operational inputs but not predicated on the ability to do so. This new focus will help facilitate greater integration between disparate unit types in a challenged communications environment while continuing to execute the commander’s intent.
Fully Connected: Looming Failure Sounds like Success
The premise of JADC2 — the capability to link the various kill chain nodes seamlessly throughout the battlespace — reads really well. Bolstered by the continuing integration of joint forces through operations in the Middle East and facing the prospect of a much larger, more capable adversary, leaders from around the Defense Department tout the need for a fully networked command and control architecture:
“Future operations in contested environments will be enabled by the networked Joint All-Domain Command and Control systems, or JADC2, capable of connecting any sensor to any shooter in any domain at any time.” — Vice Admiral Ron Boxall, requirements lead for the Joint Staff.
“Being able to get our data into those clouds is a foundational component of our strategy for JADC2 and [USAF’s Airborne Battle Management System] ABMS.” — Lieutenant General Timothy Haugh, 16th Air Force commander (Air Force’s information warfare command).
“The power of this architecture is unlocked by services, allies and partners working together to connect networks and share information at machine speed. That’s all-domain superiority.” — Preston Dunlap, Air Force chief data architect.
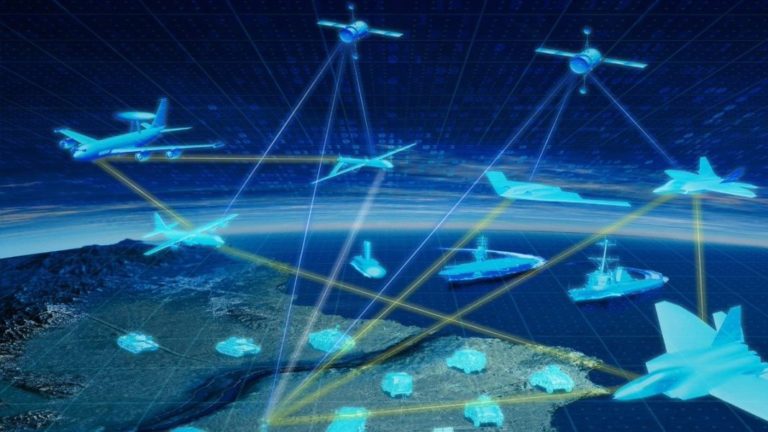
Likewise, graphics like the ones shown below illustrate the all-seeing, all-connected design of JADC2 and its various sub-components such as the USAF’s ABMS, promoted as the technical underpinning of the JADC2 concept.
(Top) USAF’s rendition of the JADC2 network, connecting assets from space, undersea, and across the battlespace. (Credit: U.S. Air Force) (Bottom) USAF’s design for its ABMS program, linking all assets to one another and including global cloud computing, as the technical underpinning of JADC2. (Credit: U.S. Air Force)
Finally, recent “on ramp” experiments that test-drive information-sharing efforts between various services are held up as proof-of-concept that this interwoven battlespace information structure is on its way to becoming reality.
But dig into each of these and one begins to see the inherent flaws that make this pursuit of an overarching integrated command and control structure across units and echelons risky. Despite nods to future warfare and what it portends, there is a significant lack of appreciation for the combat environment U.S. forces are likely to face — particularly in the western Pacific against China. Chinese military leadership writes extensively on the subject of informatized and now intelligentized warfare. Having observed and studied recent U.S. operations abroad, Chinese leaders understand the level of reliance U.S. forces have on fragile long-haul communications networks and are developing concepts of operations that explicitly attack that vulnerability as a key initial task. Yet to hear and read U.S. leadership talk of JADC2 is to hear little acknowledgement of this dynamic or what — if anything — should be adjusted in command and control networks to mitigate it. Vice Admiral Boxall’s quote at least acknowledges the contested environment that the joint force will operate in, but even then goes on to talk about “any sensor to any shooter in any domain at any time.”
As for the interconnected nature of the graphics featured above, one only need look at the capabilities China is developing and deploying on a technical level to question the feasibility of this system. Of particular concern is China’s continuing development of more capable anti-satellite systems, longer-range air-to-air and surface-to-air missiles for high-value targets — such as airborne early warning and control systems (AWACS) — and increasing cyber-attack and electronic warfare capabilities. These above images are overly optimistic and are not likely to match reality when conflict begins and these disruptive adversarial tools are deployed. And while the JADC2 experiments show that connectivity is possible, they are performed in a scripted nature and in unfettered environments: free from active countermeasures that should be expected and explored in any development cycle for a new command and control architecture.
Graceful Degradation: Salvaging a Good Idea from the Bad
How then should a realistic, cost-effective JADC2 be shaped going forward? Quite simply, the focus of JADC2 must move the discussion of degraded connectivity from the fringes and into the center. Rather than pursuing an all-seeing, operational-level network, the core tenet of this new command and control architecture should assume that groups of tactical units from different domains are more likely to operate on their own than while connected to a central operational node. Moreover, assuming data can actually reach the requisite users, a joint command and control system must ensure only the relevant and necessary information is shared and processed, rather than building up an “iron mountain” of data that dwarfs the ability to make use of it.
Realigning this core focus would then allow for greater emphasis on a variety of efforts. Perhaps most significantly, this would facilitate the creation of a more organic structure that remains flexible to the needs of its user, rather than a top-down prescriptive system. Instead of building overarching structures, like centralized clouds, and pushing for an architecture that includes every unit all the time, JADC2 developers should look at what is needed to enable discrete tactical units made up of different types of forces to come together and execute the commander’s intent. In addition to promising work like DARPA’s STITCHES program — which uses middleware to “translate” data between disparate systems — this includes things like at-the-edge processing, ensuring that shooters have organic sensors rather than relying on outside providers, and accelerating development of those systems that have a low probability of detection or intercept, such as millimeter or free-space optical waveforms.
This realignment would also facilitate the ability of forces to conduct joint exercises — not just theoretical experimentation. While events like Indo-Pacific Command’s Valiant Shield are a step in the right direction, no level of joint command and control is going to work if units from the various services do not train together regularly and robustly. Nor will these training efforts be of adequate fidelity if done mostly via tabletops or simulations. Service and combatant command leadership should prioritize live tactical integration among the various services throughout a unit’s training and deployment cycle — not in one-off annual evolutions. Likewise, operational commands should exercise regularly with fellow headquarters and with subordinate units from the other services, including training under degraded information environments.
Finally, rather than spending significant time trying to standardize a network for data transfer, a refocused JADC2 concept should move standardization of the data itself even further up the priority list. It is encouraging to see standardizing information as a noted goal of the current JADC2 effort, and it will be more critical for units to integrate among themselves. Even today there are platforms within domains that struggle to connect — and the challenge is of course even greater between services. If tactical units from different services are to create ad-hoc command networks, having the same data language is critical to make the process as seamless as possible in the time and space constraints that accompany combat operations.
JADC2’s goal of a fully immersed, across-the-battlespace network — while ambitious and well-meaning — is simply unrealistic. For those who execute command and control, the ability to connect in the best of times can often be tenuous. Layer on top of this a determined adversary with the intent to execute a systems destruction campaign — one they explicitly are designing for — and U.S. forces will find themselves lacking a holistic command and control system of the type envisioned by proponents of JADC2. Instead, much greater emphasis should be placed on designing a command and control architecture that at its core plans for a level of degradation, particularly at the operational level. A future joint command and control architecture should prioritize connectivity at the local/tactical level and focus on developing the data standardization, training exercises, and organic enablers needed to turn this from a bad idea into a good one.
CSIS does not take specific policy positions; accordingly, all views expressed above should be understood to be solely those of the author.
Photo Credit: U.S. Air Force

